Download Software What Is Google Hacking Database
Posted : adminOn 9/27/2017Remove Spyware Malware with Spy. Hunter. Top 2. 0 Countries Found to Have the Most Cybercrime. Have you ever wondered which countries face the most cybercrime If you have ever wondered which countries have the most cybercrime, then you may be surprised to know that there are few contributing factors that attract cybercriminals to specific regions of the world. Security research firm. Spam Alert Phishing Email Scam Titled Bank of America Alert Account Suspended. We recently discovered a new phishing scam from a Bank of America spam email message that attempts to warn a computer user of an invalid login resulting in a suspended banking account. The spam message is ultimately a phishing scam that tries to lure computer users to a phishing site to. Top 5 Popular Cybercrimes How You Can Easily Prevent Them. Over the course of the past few years, hackers and cybercrooks armed with sophisticated malware have stolen literally hundreds of millions of dollars from online banking accounts and individuals all over the world. We have said it many times before in recent articles, the days of robbing banks in. The Cerber Ransomware is a ransomware infection that is used to encrypt the victims files. Download Software What Is Google Hacking Databaseщ…ш§щ‡щ€' title='Download Software What Is Google Hacking Databaseщ…ш§щ‡щ€' />The Cerber Ransomware adds the extension CERBER to every file that the Cerber Ransomware encrypts. After the Cerber Ransomware has encrypted some of the files of the victim, the Cerber Ransomware demands the payment of a ransom in exchange for the decryption key. According to Cerber Ransomwares ransom note, computer users have one week to pay the ransom amount before this amount is doubled. The Cerber Ransomware Contains an Audio Message As the Cerber Ransomware encrypts the victims files, it creates TXT, HTML, and VBS files named DECRYPT MY FILES with instructions on how to pay the Cerber Ransomwares ransom. These files are dropped on every folder that contains files that were encrypted by Cerber Ransomware. According to these ransom. Posted on March 4, 2. Ransomware. The Wana. Crypt. 0r Ransomware is an encryption Trojan that features a worm like attack tactic. The Wana. Crypt. 0r Ransomware is recognized as one of the most threatening and widespread encryption Trojans up until May 1. The Wana. Crypt. 0r Ransomware managed to compromise more than hundreds of thousand systems across one hundred and forty countries on its first release to the real world. The brunt of the attack was taken by PC users in Russia and the National Healthcare System in Great Britain. The Trojan managed to block access to most of the computers connected to the National Healthcare System and nearly 7. Wana. Crypt. 0r Ransomware are recorded in Russia This password cracker is being distributed in public and anyone can download this software free of cost. Today everyone want to be secure and never want to be get. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows. Good Books on interview questions and answers for niche tech jobs at Any Top Software Company. TheINQUIRER publishes daily news, reviews on the latest gadgets and devices, and INQdepth articles for tech buffs and hobbyists. Windows Vista Para Pc De Bajos Recursos. IBM Analytics enables your organization to engage with data to answer the toughest business questions, uncover patterns and pursue breakthrough ideas. These all books based on ethical hacking tutorials not for hacking. Download Free Collection of Hacking ebook in pdf format All Hacking books in PDF format best. Download Software What Is Google Hacking Database Book' title='Download Software What Is Google Hacking Database Book' />Download Software What Is Google Hacking Database PdfPosted on March 2. Dora The Explorer Streaming Episodes here. Ransomware. The Crypto. Locker Trojan is a ransomware infection that encrypts the victims files. Crypto. Locker may typically be installed by another threat such as a Trojan downloader or a worm. Once Crypto. Locker is installed, Crypto. Locker will search for sensitive files on the victims computer and encrypt them. Essentially, Crypto. APKInspector-1.png' alt='Download Software What Is Google Hacking Database Exploid' title='Download Software What Is Google Hacking Database Exploid' />Locker takes the infected computer hostage by preventing access to any of the computer users files. Crypto. Locker then demands payment of a ransom to decrypt the infected files. Crypto. Locker is quite harmful, and ESG security analysts strongly advise computer users to use an efficient, proven and updated anti malware program to protect their computer from these types of. Posted on September 1. Ransomware. The Play bar. Ultimate search. 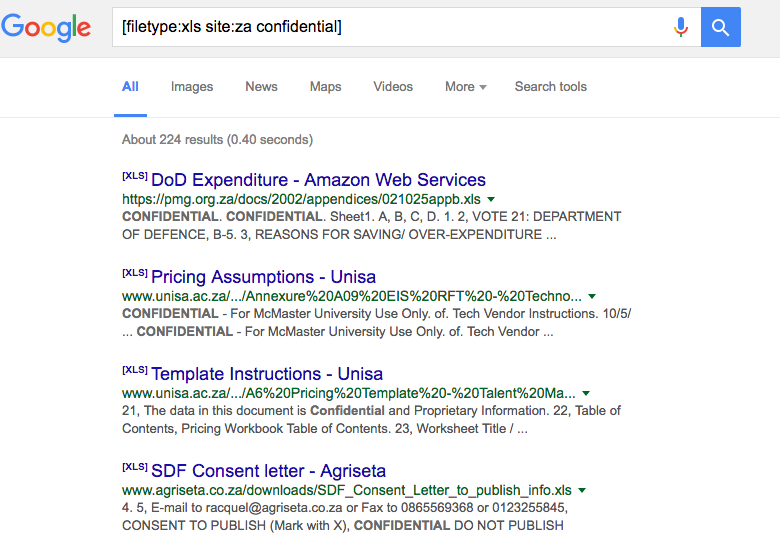 The Play bar. Blisbury LLP and features a small search bar, a weather forecast in the top right corner and a clock widget in the top left corner. Additionally, the Play bar. Adobe Flash games on online gaming platforms like. Princess Games, Games. Rockit and Tiki. Arcade. The browser hijacker related to Play bar. Apple has made its latest Mac operating system, OS X Mavericks, available to download for free from the Mac App Store. Internet traffic of infected users to Play bar. The Play bar. net browser hijacker may modify your DNS settings and change your default search aggregator, homepage and a new tab to Play bar. The Play bar. net browser hijacker might edit your Windows Registry. Posted on October 1. Browser Hijackers. The Cerber. 3 Ransomware is a new version of a well known ransomware Trojan. The Cerber Ransomware Trojan now uses a slightly different method during its attack. The main difference is that the files infected by the Cerber. Ransomware can be identified through the use of. CERBER3 as the extension that identifies the files that have been encrypted in the attack. PC security analysts had observed a Cerber. This numbering system may indicate new versions of software, and threats are no exception. The appearance of the Cerber. Ransomware indicates that the Cerber ransomware family is being developed and updated currently. The Cerber. 3 Ransomware and Possible Updates to this Threat The Cerber. Ransomware was discovered recently, around the end of August of 2. The Cerber. 3 Ransomware presents minor. Posted on September 1, 2. Ransomware. The DNS Unlocker is adware that has caught the attention of PC security researchers. Many computer users have been using programs like the DNS Unlocker to bypass region locking components in online applications. The DNS Unlocker, in particular, has been advertised as a way for computer users to access Netflix for regions outside of their location. PC security analysts strongly recommend against this approach. There are numerous applications available that supposedly allow computer users to modify their IP or connect to certain websites that are blocked for certain regions. However, this is a common way for adware developers to distribute their low level and mid level threats. In several situations, it may be better to avoid using these types of components or looking for reputable options even if they are slightly more expensive than. Posted on June 1. Adware. Tavanero. PUP Potentially Unwanted Program. Tavanero. info attempts to mimic the look and feel of the Google search engine to mislead computer users. Tavanero. info uses the Google logo colors in its layout and even includes the term Google. TM Custom Search, despite the fact that Tavanero. Google. Tavanero. There is no legitimate connection between Tavanero. Google, despite this fake search engines claims. The Activities of Tavanero. Its Associated PUP Tavanero. PUP known as a browser hijacker, mainly because these components may be used to hijack. Crack Autodesk Inventor 2011 on this page. Posted on September 6, 2. Browser Hijackers. If Tech connect. Then you wonder how it could have happened if wasnt you who introduced Tech connect. The answer is very simple browser hijackers may be part of the installation of a free software you downloaded from the Web recently. This is a well used method since the computer users may be in a hurry when installing the free program they need and instead of choosing Advanced or Custom, used the quickest installation method, skipping its EULA and additional details, giving the browser hijacker, adware, and PUPs, the permission to be installed unknowingly. Although not threatening, Tech connect. Posted on September 1. Browser Hijackers. The Zepto Ransomware is a variant of the Trojan Locky Ransomware. The Zepto Ransomware is designed to infect all versions of the Windows operating system, from Windows XP all the way to Windows 1. Ransomware Trojans like the Zepto Ransomware are especially threatening because, even if removed, the victims files will still be inaccessible.
The Play bar. Blisbury LLP and features a small search bar, a weather forecast in the top right corner and a clock widget in the top left corner. Additionally, the Play bar. Adobe Flash games on online gaming platforms like. Princess Games, Games. Rockit and Tiki. Arcade. The browser hijacker related to Play bar. Apple has made its latest Mac operating system, OS X Mavericks, available to download for free from the Mac App Store. Internet traffic of infected users to Play bar. The Play bar. net browser hijacker may modify your DNS settings and change your default search aggregator, homepage and a new tab to Play bar. The Play bar. net browser hijacker might edit your Windows Registry. Posted on October 1. Browser Hijackers. The Cerber. 3 Ransomware is a new version of a well known ransomware Trojan. The Cerber Ransomware Trojan now uses a slightly different method during its attack. The main difference is that the files infected by the Cerber. Ransomware can be identified through the use of. CERBER3 as the extension that identifies the files that have been encrypted in the attack. PC security analysts had observed a Cerber. This numbering system may indicate new versions of software, and threats are no exception. The appearance of the Cerber. Ransomware indicates that the Cerber ransomware family is being developed and updated currently. The Cerber. 3 Ransomware and Possible Updates to this Threat The Cerber. Ransomware was discovered recently, around the end of August of 2. The Cerber. 3 Ransomware presents minor. Posted on September 1, 2. Ransomware. The DNS Unlocker is adware that has caught the attention of PC security researchers. Many computer users have been using programs like the DNS Unlocker to bypass region locking components in online applications. The DNS Unlocker, in particular, has been advertised as a way for computer users to access Netflix for regions outside of their location. PC security analysts strongly recommend against this approach. There are numerous applications available that supposedly allow computer users to modify their IP or connect to certain websites that are blocked for certain regions. However, this is a common way for adware developers to distribute their low level and mid level threats. In several situations, it may be better to avoid using these types of components or looking for reputable options even if they are slightly more expensive than. Posted on June 1. Adware. Tavanero. PUP Potentially Unwanted Program. Tavanero. info attempts to mimic the look and feel of the Google search engine to mislead computer users. Tavanero. info uses the Google logo colors in its layout and even includes the term Google. TM Custom Search, despite the fact that Tavanero. Google. Tavanero. There is no legitimate connection between Tavanero. Google, despite this fake search engines claims. The Activities of Tavanero. Its Associated PUP Tavanero. PUP known as a browser hijacker, mainly because these components may be used to hijack. Crack Autodesk Inventor 2011 on this page. Posted on September 6, 2. Browser Hijackers. If Tech connect. Then you wonder how it could have happened if wasnt you who introduced Tech connect. The answer is very simple browser hijackers may be part of the installation of a free software you downloaded from the Web recently. This is a well used method since the computer users may be in a hurry when installing the free program they need and instead of choosing Advanced or Custom, used the quickest installation method, skipping its EULA and additional details, giving the browser hijacker, adware, and PUPs, the permission to be installed unknowingly. Although not threatening, Tech connect. Posted on September 1. Browser Hijackers. The Zepto Ransomware is a variant of the Trojan Locky Ransomware. The Zepto Ransomware is designed to infect all versions of the Windows operating system, from Windows XP all the way to Windows 1. Ransomware Trojans like the Zepto Ransomware are especially threatening because, even if removed, the victims files will still be inaccessible.
